Online Privacy and Safety

Be Safe Accordion Open
Resources:
An Online Privacy and Safety Podcast
In this training session, we dive deep into the world of online privacy and safety, focusing on practical steps and strategies for protecting personal information. From understanding data collection practices to navigating common online risks like phishing and cyberbullying, this guide offers essential tools and techniques to keep your online experiences secure. Looking to improve your digital safety? This session covers everything from secure passwords and privacy settings to identifying harmful content. Stay informed and take control of your online privacy today!
Surveillance capitalism image from Dr. Ayesha Khan and Sprank on Cosmic Anarchy
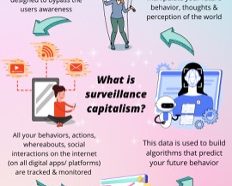
-Digital footprints from social media and communication platforms
Resource:
Check “Results about you” to learn what people can find out about you from Google
Doxxing yourself activity from NYT
-Safe internet browsing and searching
Resource:
Use NordVPN Link Checker to check if a website or link is safe
6 ways to check if a website or link is safe!
Safe online surfing game from the FBI!
Be Secure Accordion Closed
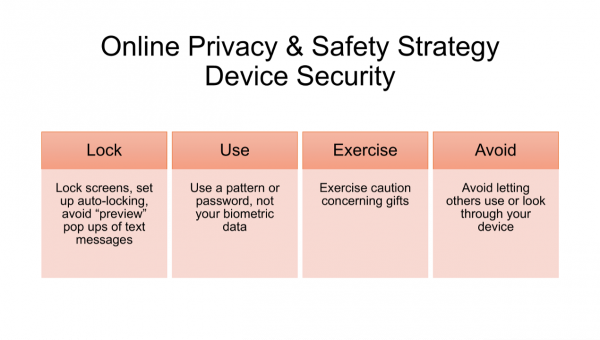
-Privacy and Safety in Online Transactions & Interactions (passwords, dual authentication, securing devices)
Resource:
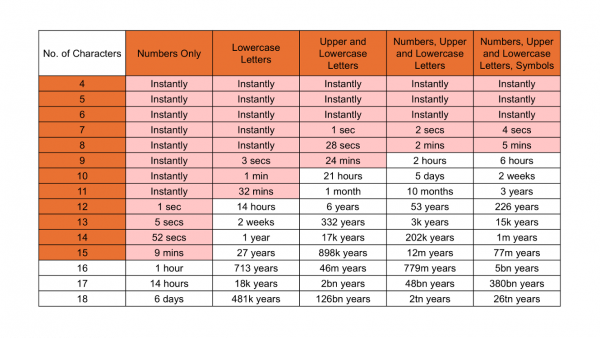
Activity: How long it takes to crack a password; Best practices for passwords

Two-Factor Authentication, or 2FA. This is an extra layer of security for your accounts. With 2FA, even if someone has your password, they still need a second piece of information to log in, like a code sent to your phone. This way, even if your password gets leaked, your account is still protected. The 2FA Directory website is a simple, community-run tool that shows which websites and online services support two-factor authentication (2FA), such as text messages, authenticator apps, or security keys. You can search for a service to see what types of extra login protection it offers, helping you make safer choices online.
A VPN (Virtual Private Network) creates a secure connection for you to go online, which makes it harder for hackers or anyone else to see what websites you’re visiting or what information you’re sharing.
Think of it like a private tunnel between your device and the internet. It’s especially helpful when you’re using public Wi-Fi, like in a coffee shop or airport, because public networks can be easy targets for hackers.
-Securing your device
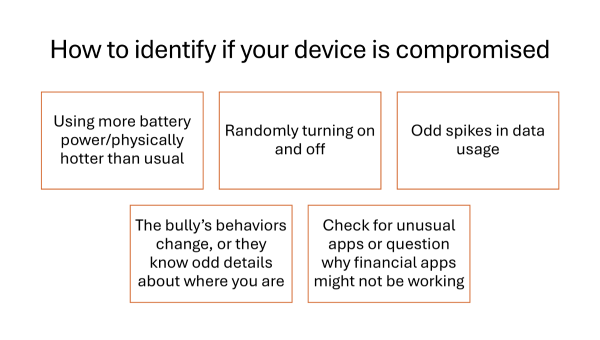
Social media security and privacy checklist from NYT
-Messaging and email safety (phishing/spotting scams)
Resources: interactive scam cards from claude ai;
Type of Scams and spotting phishing
have I been pwned for email and for passwords
sign up for notifications to know when your information is breached
Be Ready Accordion Closed
-Cyberbullying Awareness and Response
Cyberbullying is when someone says mean or hurtful things to others online. This can happen through messages, comments, or posts. If someone is bullying you or someone else online, don’t respond or argue back. Instead, communicate this to a trusted friend/family member and move through the actions that you can take. Restrict, block, and report.
Sometimes, we might see things online that are inappropriate or make us feel uneasy. If this happens, don’t stay on that website or app. Leave it right away. Tell a trusted friend or family member so they can help you avoid similar content in the future.
Let’s talk about spotting harmful content. Harmful content can include fake profiles, hurtful comments, spam, or people pretending to be someone they’re not. Some clues that a profile might be fake include a lack of personal posts, a small number of friends or followers, and a strange or generic profile picture. If something or someone seems suspicious, it’s worth looking a bit closer.
Once you spot harmful content, the next step is to report it. Most social media platforms have a simple way to report things that break their rules, like fake accounts or bad comments. You can usually find the report option by clicking on the profile or post and selecting ‘Report.’ Reporting helps the platform review and remove harmful content, so others don’t have to see it.
If someone is bothering you, you can also block them. When you block someone, they can’t see your profile, send you messages, or interact with you. Blocking is a good option if you want to protect your space and make sure that person can’t contact you again. To block someone, go to their profile, click on the settings or options button, and select ‘Block.’
-Digital Citizenship
Resource:
Digital citizenship and online awareness with Roblox and Google Game
Other resources:
Southwest Autism Research and Resource Center (SARRC) Online Privacy and Safety Manual
Family online safety institute – resource for parents!
If you feel you are the target of bullying, stalking, harassment, or abuse

This contract is supported by the Administration for Community Living (ACL) of the Department of Health and Human Services (HHS) as part of an award totaling $1,500,930, with 0% from non-governmental sources. Services provided under contract, including the views expressed in written materials or publications and by any speakers, do not necessarily reflect the official policies of the ADDPC, ACL, or HHS.